
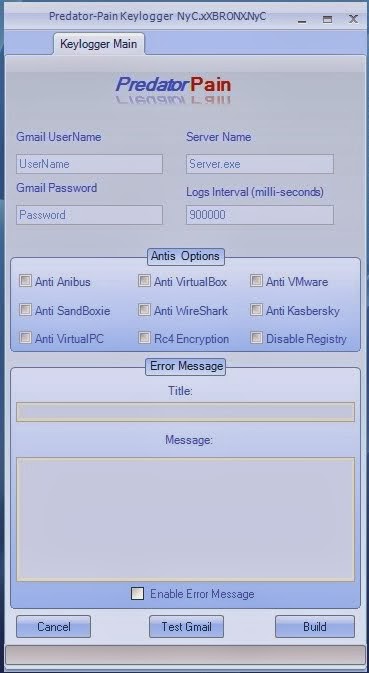
Keylogger Download Full Version
A Trend Micro research paper that reveals the operations and cybercriminals behind Predator Pain and Limitless Keylogger, which are malware toolkits that are easily obtained from underground forums. Predator Pain is a premium keylogger which is used by cybercriminals and hackers to steal keystrokes from unaware victims. The Predator Pain (Predator 13) keylogger has been analyzed by MalwareConfig and they have published various PredatorPain samples which can be used for analysis. HawkEye is yet another off-the-shelf crimeware with close ties to Predator Pain and Limitless - keyloggers used in campaigns that also targeted SMBs in 2014. Piercing the HawkEye: Nigerian Cybercriminals Use a Simple Keylogger to Prey on SMBs Worldwide. Piercing the HawkEye: Nigerian Cybercriminals Use a Simple Keylogger to Prey on SMBs.
Keylogger Software

Keylogger Download Rapidshare
- Predator Pain Keylogger - Partial Dump Of Strings In Memory
- http://stopmalvertising.com/malware-reports/analysis-of-the-predator-pain-keylogger.html
- 0x230448 (28): MACHINE_CONFIG
- 0x249c48 (20): System.Windows.Forms
- 0x249dc8 (16): GDI+ Hook Window
- 0x249ee8 (21): Microsoft.VisualBasic
- 0x24c540 (14): KazyLoader.dll
- 0x1991ff9 (44): !This program cannot be run in DOS mode.
- 0x199279a (14): KazyLoader.dll
- 0x199300a (30): VS_VERSION_INFO
- 0x1993086 (22): Translation
- 0x19930e6 (22): CompanyName
- 0x199313c (20): KazyLoader
- 0x199318a (24): InternalName
- 0x19931ca (28): LegalCopyright
- 0x19931fe (30): Microsoft 2014
- 0x1993248 (28): KazyLoader.dll
- 0x1993288 (20): KazyLoader
- 0x19932da (32): Assembly Version
- 0x19983a8 (24): winlogon.exe
- 0x19983ec (116): The application failed to initialize properly (0xc0000135)
- 0x1998580 (34): HKEY_CURRENT_USER
- 0x19985e8 (20): HKEY_USERS
- 0x199864c (38): HKEY_CURRENT_CONFIG
- 0x1998890 (106): SoftwareMicrosoftWindows NTCurrentVersionWinlogon
- 0x1998958 (116): SoftwareMicrosoftWindowsCurrent VersionPoliciesSystem
- 0x1998a68 (40): -reg 'explorer.exe,
- 0x199cc48 (38): LOADER_OPTIMIZATION
- 0x199cda4 (88): SoftwareMicrosoftWindows NTCurrentVersion
- 0x199ce64 (22): Server Core
- 0x19b58b4 (22): dontclearff
- 0x19b592c (28): websitevisitor
- 0x19b598c (36): DisableAdminRights
- 0x19b5b04 (22): Disablemelt
- 0x19b5b54 (20): Disablecmd
- 0x19b5bac (32): Disablespreaders
- 0x19b5c0c (38): Windows Update.exe
- 0x19b6935 (44): !This program cannot be run in DOS mode.
- 0x19b7252 (18): CMemoryExecute.dll
- 0x19b78d1 (14): CMemoryExecute
- 0x19b7d46 (30): VS_VERSION_INFO
- 0x19b7dc2 (22): Translation
- 0x19b7e22 (30): FileDescription
- 0x19b7e6a (22): FileVersion
- 0x19b7eb4 (36): CMemoryExecute.dll
- 0x19b7f00 (20): Copyright
- 0x19b7f4c (36): CMemoryExecute.dll
- 0x19b7f94 (28): CMemoryExecute
- 0x19b7fee (32): Assembly Version
- 0x19bb738 (36): WindowsUpdate.exe
- 0x19bb7bc (22): pidloc.txt
- 0x19bb814 (30): Disablestealers
- 0x19bb898 (22): Disableclip
- 0x19c011c (58): results@facebookmarketers.net
- 0x19c01d0 (24): ftp.host.com
- 0x19c02bc (98): http://www.DeceptiveEngineering.com/path/logs.php
- 0x19c04b0 (26): GetHostByName
- 0x19c054c (44): <!-- do not script -->
- 0x19c0734 (26): net_webclient
- 0x19c09b0 (20): WebRequest
- 0x19c1e84 (28): HttpWebRequest
- 0x19c216c (20): bypasslist
- 0x19c2584 (20): autoDetect
- 0x19c25dc (26): bypassonlocal
- 0x19c2634 (32): usesystemdefault
- 0x19c4e4c (56): http://whatismyipaddress.com
- 0x19cb7ec (60): SELECT * FROM AntivirusProduct
- 0x19cb884 (24): COMPUTERNAME
- 0x19cc048 (28): //./root/cimv2
- 0x19cd7ac (30): Disablefakerror
- 0x19ce324 (38): bitcoinwallet.dat
- 0x19ce384 (20): wallet.dat
- 0x19ce748 (28): Disablestartup
- 0x19ce778 (90): SoftwareMicrosoftWindowsCurrentVersionRun
- 0x19cffd4 (72): This is an email notifying you that
- 0x19d0030 (262): has ran your logger and emails should be sent to you shortly and at interval choosen.
- Predator Logger Details:
- 0x19d0148 (42):
- 0x19d0184 (56):
- 0x19d01d0 (74):
- 0x19d022c (62): minutes
- Stealers Enabled:
- Time Log will be delivered: Average 2 to 4 minutes
- Local Date and Time:
- Installed Language:
- Operating System:
- Internal IP Address:
- External IP Address:
- Installed Anti-Virus:
- Installed Firewall:
- 0x19d04d8 (60): Predator_Painv13_Notification_
- 0x19d0544 (68): Predator Pain v13 - Server Ran - [
- 0x19d05d8 (78): Predator Pain v13|Minecraft Stealer - [
- 0x19d0638 (312): There is a file attached to this email containing Minecraft username and password download it then decrypt the login information with my Minecraft Decryptor
- 0x19d09b4 (42): Win32_OperatingSystem
- 0x19d0fcc (70): select * from Win32_OperatingSystem
- 0x19d13f8 (46): DeviceIndependentBitmap
- 0x19d148c (24): MetaFilePict
- 0x19d14e4 (42): DataInterchangeFormat
- 0x19d1648 (22): HTML Format
- 0x19d16a4 (32): PersistentObject
- 0x19d1704 (60): WindowsForms10PersistentObject
- 0x19d1904 (72): Predator Pain v13 - Key Recorder - [
- 0x19d1960 (454): **********************************************
- **********************************************
- 0x19d1b38 (458):
- Keylogger Log
- 0x19d1d64 (36): screensscreenshot
- 0x19d2ebc (48): specifiedPickupDirectory
- 0x19d32f8 (36): defaultCredentials
- 0x19d33a4 (20): targetName
- 0x19d3938 (46): pickupDirectoryLocation
- 0x19d4010 (68): SMTPSVC/mail.facebookmarketers.net
- 0x19d4784 (56): MailAddressUnsupportedFormat
- 0x19d48a8 (42): facebookmarketers.net
- 0x19d4904 (90): Predator Pain v13 - Server Ran - [SOME-PC]
- 0x19db7e0 (30): DeliveryMethod=
- 0x19dbafc (72): ByHost:mail.facebookmarketers.net:25
- 0x19dbbd8 (72): ByHost:mail.facebookmarketers.net:25
- 25
- 0x19dc5b4 (42): facebookmarketers.net
- 0x19dc7d4 (84): Microsoft.NETFrameworkv2.0.50727vbc.exe
- 0x19dc8a8 (28): holdermail.txt
- 0x1b69360 (486): **********************************************
- **********************************************
- 0x1b69558 (46):
- 0x1b69598 (30):
- 0x1b695c8 (58):
- 0x1b69614 (56):
- 0x1b69660 (466):
- WEB Browser Password Recovery
- **********************************************
- **********************************************
- 0x1b69a2c (930):
- Internet Download Manager Recovery
- **********************************************
- **********************************************
- 0x1b69e2c (66): Predator Pain v13|Stealer Log - [
- 0x1b69eac (24): holderwb.txt
- 0x1df1ff0 (70): select * from Win32_OperatingSystem
- 0x1e15db4 (72): f:ddToolsdevdivEcmaPublicKey.snk
- 0x1e24a8c (76): Unable to connect to the remote server
- 0x1e24de8 (42): Failure sending mail.
- 0x1e327c0 (74): Pain File Stealer Bitcoin Stealer - [
- 0x1e3281c (128): Steals the Wallet.DAT file that holds the users bitcoin currency
- 0x2996e2d (44): !This program cannot be run in DOS mode.
- 0x299932f (44): !This program cannot be run in DOS mode.
- 0x299e3e8 (36): WebBrowserPassView
- 0x299e473 (44): !This program cannot be run in DOS mode.
- 0x299ed90 (18): CMemoryExecute.dll
- 0x299f40f (14): CMemoryExecute
- 0x299f57a (121): C:UsersJovanDocumentsVisual Studio 2010ProjectsStealerCMemoryExecuteCMemoryExecuteobjReleaseCMemoryExecute.pdb
- 0x299f8e0 (22): VarFileInfo
- 0x299f924 (28): StringFileInfo
- 0x299f982 (28): CMemoryExecute
- 0x299f9d8 (24): InternalName
- 0x299fa20 (28): LegalCopyright
- 0x299fa68 (32): OriginalFilename
- 0x299fab8 (22): ProductName
- 0x299faf8 (28): ProductVersion
- 0x299fe78 (44): !This program cannot be run in DOS mode.
- 0x29e24ef (36): WebBrowserPassView
- 0x29e2543 (82): Apple ComputerPreferenceskeychain.plist
- 0x29e25e3 (27): com.apple.WebKit2WebProcess
- 0x29e260b (138): SELECT origin_url, action_url, username_element, username_value, password_element, password_value, signon_realm, date_created from logins
- 0x29e272b (40): LoadPasswordsFirefox
- 0x29e277f (36): LoadPasswordsOpera
- 0x29e27cf (44): LoadPasswordsSeaMonkey
- 0x29e282f (46): UseFirefoxInstallFolder
- 0x29e288f (40): UseOperaPasswordFile
- 0x29e28e7 (40): FirefoxInstallFolder
- 0x29e293b (34): OperaPasswordFile
- 0x29e2962 (57): 'Account','Login Name','Password','Web Site','Comments'
- 0x29e2c0f (11): CredDeleteA
- 0x29e2c2b (14): CredEnumerateW
- 0x29e2c53 (18): CryptUnprotectData
- 0x29e2c7f (19): CryptReleaseContext
- 0x29e2ca3 (17): CryptGetHashParam
- 0x29e2cc7 (16): CryptDestroyHash
- 0x29e32ef (15): SQLite format 3
- type text,
- tbl_name text,
- sql text
- 0x29e707b (130): SOFTWAREMicrosoftWindowsCurrentVersionApp Pathsseamonkey.exe
- 0x29e7133 (32): SOFTWAREMozilla
- 0x29e71cb (129): SELECT id, hostname, httpRealm, formSubmitURL, usernameField, passwordField, encryptedUsername, encryptedPassword FROM moz_logins
- 0x29e726f (24): signons2.txt
- 0x29e72a7 (28): signons.sqlite
- 0x29e7553 (84): MicrosoftWindowsWebCacheWebCacheV01.dat
- 0x29e75ab (84): MicrosoftWindowsWebCacheWebCacheV24.dat
- 0x29e7633 (116): SoftwareMicrosoftInternet ExplorerIntelliFormsStorage2
- 0x29e76ab (88): https://www.google.com/accounts/servicelogin
- 0x29e773b (72): https://login.yahoo.com/config/login
- 0x29e77d7 (22): :stringdata
- 0x29e7e79 (24): @history.dat
- 0x29e7eaf (32): MozillaProfiles
- 0x29e7f07 (52): MozillaSeaMonkeyProfiles
- 0x29e7f63 (30): MozillaFirefox
- 0x29e8157 (22): sqlite3.dll
- 0x29e819b (12): NSS_Shutdown
- 0x29e81c3 (13): PK11_FreeSlot
- 0x29e81eb (17): PK11_Authenticate
- 0x29e82df (20): Login Data
- 0x29e8327 (54): GoogleChrome SxSUser Data
- 0x29e838b (58): OperaOpera7profilewand.dat
- 0x29e859b (20): PStoreCreateInstance
- 0x29ebb43 (22): ProductName
- 0x29ebb7b (22): FileVersion
- 0x29ebbb3 (22): CompanyName
- 0x29ebbe7 (28): LegalCopyright
- 0x29ebc2b (22): log profile
- 0x29ebc83 (14): VaultOpenVault
- 0x29ebca3 (19): VaultEnumerateItems
- 0x29ebcd7 (12): VaultGetItem
- 0x29ebd3b (68): f:ProjectsVS2005WebBrowserPassViewReleaseWebBrowserPassView.pdb
- 0x29f2eff (44): Load Passwords From...
- 0x29f2f8f (26): Google Chrome
- 0x29f30e7 (30): Firefox Options
- 0x29f3187 (32): Firefox Profile:
- 0x29f32a3 (28): Chrome Options
- 0x29f336b (26): Opera Options
- 0x29f38a5 (50): Select a filename to save
- 0x29f38d9 (382): Web Browser Passwords%Choose another Firefox profile folder)Choose the installation folder of Firefox,Choose another profile of Chrome Web browser,Choose the password file of Opera (wand.dat)
- Loading... %d
- 0x29f3a97 (46): Tab Delimited Text File
- 0x29f3aeb (44): HTML File - Horizontal
- 0x29f3b55 (50): Comma Delimited Text File
- 0x29f3bbf (58): Opera Password File All Files
- 0x29f3c53 (54): Internet Explorer 7.0 - 9.0
- 0x29f3ca3 (22): Firefox 2.x
- 0x29f3d0b (64): Internet Explorer 10.0 SeaMonkey
- 0x29f3dbd (34): Password Strength
- 0x29f3e01 (28): Password Field
- 0x29f3e65 (22): Very Strong
- 0x29f3fd1 (28): StringFileInfo
- 0x29f403d (30): FileDescription
- 0x29f408d (22): FileVersion
- 0x29f40d3 (36): WebBrowserPassView
- 0x29f411f (20): Copyright
- 0x29f4169 (32): OriginalFilename
- 0x29f41c1 (22): ProductName
- 0x29f4209 (28): ProductVersion
- 0x29f4259 (22): Translation
- 0x29f5cdd (44): !This program cannot be run in DOS mode.
- 0x2a07088 (14): POP3 User Name
- 0x2a070a8 (18): HTTPMail User Name
- 0x2a070cc (11): POP3 Server
- 0x2a070e4 (15): HTTPMail Server
- 0x2a07100 (14): POP3 Password2
- 0x2a07120 (18): HTTPMail Password2
- 0x2a0715c (13): HTTPMail Port
- 0x2a07190 (22): IMAP Secure Connection
- 0x2a071c4 (22): SMTP Secure Connection
- 0x2a071f0 (18): SMTP Email Address
- 0x2a07214 (13): IMAP Password
- 0x2a07234 (13): SMTP Password
- 0x2a07290 (12): POP3 Use SPA
- 0x2a072b0 (16): HTTPMail Use SSL
- 0x2a072d4 (12): Display Name
- 0x2a07304 (52): SoftwareMicrosoftInternet Account ManagerAccounts
- 0x2a07344 (62): SoftwareMicrosoftOfficeOutlookOMI Account ManagerAccounts
- 0x2a07390 (12): EmailAddress
- 0x2a073c0 (12): PopLogSecure
- 0x2a073dc (11): SMTPAccount
- 0x2a07400 (13): SMTPLogSecure
- 0x2a07420 (31): SoftwareIncrediMailIdentities
- 0x2a07488 (13): ReturnAddress
- 0x2a074ac (13): Personalities
- 0x2a074cc (13): ESMTPUsername
- 0x2a074ec (10): POP3Server
- 0x2a07508 (12): POP3Password
- 0x2a07524 (19): SoftwareGroup Mail
- 0x2a07550 (12): %s@yahoo.com
- 0x2a07563 (57): 'Account','Login Name','Password','Web Site','Comments'
- 0x2a075b0 (100): www.google.com/Please log in to your Gmail account
- 0x2a07618 (108): www.google.com:443/Please log in to your Gmail account
- 0x2a07688 (102): www.google.com/Please log in to your Google Account
- 0x2a076f0 (110): www.google.com:443/Please log in to your Google Account
- 0x2a07760 (55): SoftwareMicrosoftWindows Messaging SubsystemProfiles
- 0x2a07798 (81): SoftwareMicrosoftWindows NTCurrentVersionWindows Messaging SubsystemProfiles
- 0x2a077ec (47): SoftwareMicrosoftOffice15.0OutlookProfiles
- 0x2a07b28 (16): POP3_credentials
- 0x2a07b54 (40): SoftwareGoogleGoogle DesktopMailboxes
- 0x2a07b84 (36): SoftwareGoogleGoogle TalkAccounts
- 0x2a08024 (20): mail.account.account
- 0x2a08050 (11): mail.server
- 0x2a08098 (13): mail.identity
- 0x2a080d8 (10): mailbox://
- 0x2a080fc (12): imap://%s@%s
- 0x2a08110 (129): SELECT id, hostname, httpRealm, formSubmitURL, usernameField, passwordField, encryptedUsername, encryptedPassword FROM moz_logins
- 0x2a081b0 (11): signons.txt
- 0x2a081f4 (30): Password.NET Messenger Service
- 0x2a08230 (31): SoftwareMicrosoftMSNMessenger
- 0x2a08250 (35): SoftwareMicrosoftMessengerService
- 0x2a0828c (11): ps:password
- 0x2a082c0 (17): windowslive:name=
- 0x2a08eec (11): *.oeaccount
- 0x2a08f10 (28): MicrosoftWindows Live Mail
- 0x2a08f48 (20): SoftwareYahooPager
- 0x2a08fd8 (44): f:ProjectsVS2005mailpvReleasemailpv.pdb
- 0x2a0d588 (30): Outlook Express
- 0x2a0d5ce (52): Group Mail Free
- 0x2a0d604 (60): MS Outlook 2002/2003/2007/2010
- 0x2a0d666 (50): Yahoo! Mail
- 0x2a0d69a (22): Thunderbird
- 0x2a0d6d0 (24): Windows Mail
- 0x2a0d70e (24): Outlook 2013
- 0x2a0d96a (30): VS_VERSION_INFO
- 0x2a0da02 (22): CompanyName
- 0x2a0da54 (44): Mail Password Recovery
- 0x2a0dab6 (24): InternalName
- 0x2a0daf2 (28): LegalCopyright
- 0x2a0db26 (44): 2003 - 2013 Nir Sofer
- 0x2a0db7c (20): mailpv.exe
- 0x2a0dbb4 (26): Mail PassView
- 0x2a0dc06 (22): VarFileInfo
- 0x2a10bba (19): encryptedpassstring
- 0x2a10be2 (10): portstring
- 0x2a10bf9 (13): fakemgrstring
- 0x2a10c18 (16): encryptedftpuser
- 0x2a10c3a (16): encryptedphplink
- 0x2a10c8e (14): websitevisitor
- 0x2a10cac (11): AdminRights
- 0x2a10ce8 (11): TaskManager
- 0x2a10d39 (10): Minecraftt
- 0x2a10d71 (32): AccessedThroughPropertyAttribute
- 0x2a10d9e (10): passstring
- 0x2a10e0f (10): WM_KEYDOWN
- 0x2a10e28 (11): WM_SYSKEYUP
- 0x2a10e43 (26): LastCheckedForegroundTitle
- 0x2a10e8d (10): MyFirewall
- 0x2a10eb1 (18): CleanedPasswordsWB
- 0x2a1157b (10): DeleteFile
- 0x2a1159f (17): SetApartmentState
- 0x2a115cb (13): IsNullOrEmpty
- 0x2a115f2 (13): WriteAllBytes
- 0x2a11614 (12): DownloadFile
- 0x2a116e7 (18): GetProcessesByName
- 0x2a11746 (16): NetworkInterface
- 0x2a1178d (24): get_NetworkInterfaceType
- 0x2a117bb (21): get_OperationalStatus
- 0x2a117e3 (21): IsConnectedToInternet
- 0x2a11855 (11): MailMessage
- 0x2a11871 (10): SmtpClient
- 0x2a118bd (12): ComputerInfo
- 0x2a118e1 (11): CultureInfo
- 0x2a11902 (14): get_OSFullName
- 0x2a1192d (21): MailAddressCollection
- 0x2a11961 (13): set_EnableSsl
- 0x2a11981 (10): System.Net
- 0x2a1199c (18): ICredentialsByHost
- 0x2a119c2 (12): get_Registry
- 0x2a119e6 (17): RegistryValueKind
- 0x2a11b09 (24): DESCryptoServiceProvider
- 0x2a11c92 (11): get_Version
- 0x2a11cb5 (13): get_OSVersion
- 0x2a11cdd (12): StreamReader
- 0x2a11d24 (24): WaitUntilFileIsAvailable
- 0x2a11d56 (20): AttachmentCollection
- 0x2a11d8e (12): MemoryStream
- 0x2a11da6 (21): System.IO.Compression
- 0x2a11e22 (12): Minecraftsub
- 0x2a11ef2 (11): SendLogsFTP
- 0x2a11f0c (12): BinaryWriter
- 0x2a11f2b (12): ICredentials
- 0x2a11f43 (16): GetRequestStream
- 0x2a11f70 (11): SendLogsPHP
- 0x2a11f95 (13): get_TimeOfDay
- 0x2a11fb1 (14): ClipboardProxy
- 0x2a1213c (13): GetExternalIP
- 0x2a12203 (12): GetAntiVirus
- 0x2a1223a (15): KBDLLHOOKSTRUCT
- 0x2a127d5 (11): set_Culture
- 0x2a127fe (10): get_mailpv
- 0x2a12828 (14): CMemoryExecute
- 0x2a1319d (22): dontclearff
- 0x2a131e5 (28): websitevisitor
- 0x2a13221 (36): DisableAdminRights
- 0x2a132ed (22): Disablemelt
- 0x2a1331b (20): Disablecmd
- 0x2a13351 (32): Disablespreaders
- 0x2a1338d (38): Windows Update.exe
- 0x2a13659 (22): SysInfo.txt
- 0x2a1369b (28): PredatorLogger
- 0x2a136d9 (26): Disablelogger
- 0x2a13779 (50): MozillaFirefoxProfiles
- 0x2a137e1 (20): 127.0.0.1
- 0x2a13839 (40): ClientRegistry.blob
- 0x2a1388f (54): Microsoft Application Error
- 0x2a138dd (72): This is an email notifying you that
- 0x2a13928 (262): has ran your logger and emails should be sent to you shortly and at interval choosen.
- Predator Logger Details:
- 0x2a13a30 (42):
- 0x2a13a5c (56):
- 0x2a13a96 (74):
- 0x2a13ae2 (62): minutes
- Stealers Enabled:
- Time Log will be delivered: Average 2 to 4 minutes
- Local Date and Time:
- Installed Language:
- Operating System:
- Internal IP Address:
- External IP Address:
- Installed Anti-Virus:
- Installed Firewall:
- 0x2a13cf5 (60): Predator_Painv13_Notification_
- 0x2a13d3d (68): Predator Pain v13 - Server Ran - [
- 0x2a13d84 (154): HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionExplorerAdvanced
- 0x2a13e5a (24): open=Sys.exe
- 0x2a13ea6 (90): SoftwareMicrosoftWindowsCurrentVersionRun
- 0x2a13f20 (28): CMemoryExecute
- 0x2a13f46 (106): C:WindowsMicrosoft.NETFrameworkv2.0.50727vbc.exe
- 0x2a13ffa (22): _wallet.dat
- 0x2a1403a (84): Microsoft.NETFrameworkv2.0.50727vbc.exe
- 0x2a140c2 (28): holdermail.txt
- 0x2a140e1 (486): **********************************************
- **********************************************
- 0x2a142c9 (46):
- 0x2a142f9 (30):
- 0x2a14319 (58):
- 0x2a14355 (56):
- 0x2a14390 (466):
- WEB Browser Password Recovery
- **********************************************
- **********************************************
- 0x2a1473c (930):
- Internet Download Manager Recovery
- **********************************************
- **********************************************
- 0x2a14b1c (66): Predator Pain v13|Stealer Log - [
- 0x2a14b7c (24): holderwb.txt
- 0x2a14b96 (74): Pain File Stealer Bitcoin Stealer - [
- 0x2a14be3 (128): Steals the Wallet.DAT file that holds the users bitcoin currency
- 0x2a14c91 (78): Predator Pain v13|Minecraft Stealer - [
- 0x2a14ce2 (312): There is a file attached to this email containing Minecraft username and password download it then decrypt the login information with my Minecraft Decryptor
- 0x2a14e84 (72): Predator Pain v13 - Key Recorder - [
- 0x2a14ecf (454): **********************************************
- **********************************************
- 0x2a15098 (458):
- Keylogger Log
- 0x2a15292 (36): screensscreenshot
- 0x2a1532e (26): [------------
- 0x2a15366 (26): 099u787978786
- 0x2a153be (44): <!-- do not script -->
- 0x2a1542a (60): SELECT * FROM AntivirusProduct
- 0x2a15480 (58): SELECT * FROM FirewallProduct
- 0x2a154f2 (36): WebBrowserPassView
- 0x2a15520 (104): :WindowsMicrosoft.NETFrameworkv2.0.50727vbc.exe
- 0x2a2d464 (106): SoftwareMicrosoftWindows NTCurrentVersionWinlogon
- 0x2a2d4fa (116): SoftwareMicrosoftWindowsCurrent VersionPoliciesSystem
- 0x2a2d5b6 (40): -reg 'explorer.exe,
- 0x2a2d638 (22): SbieDll.dll